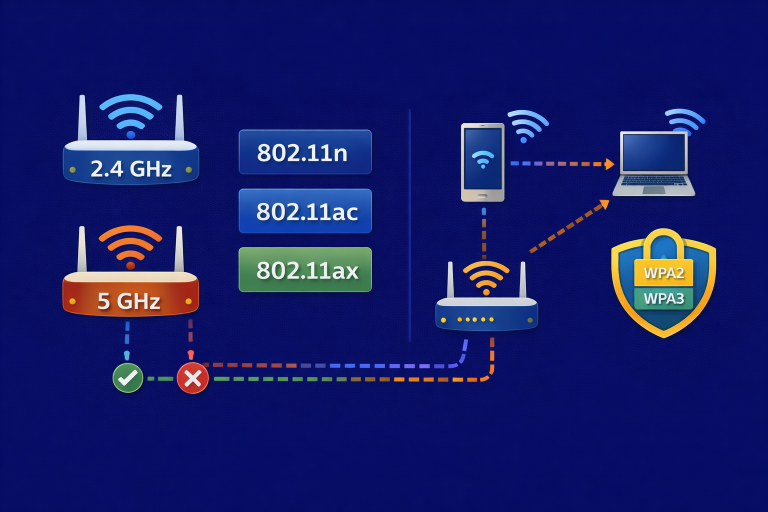
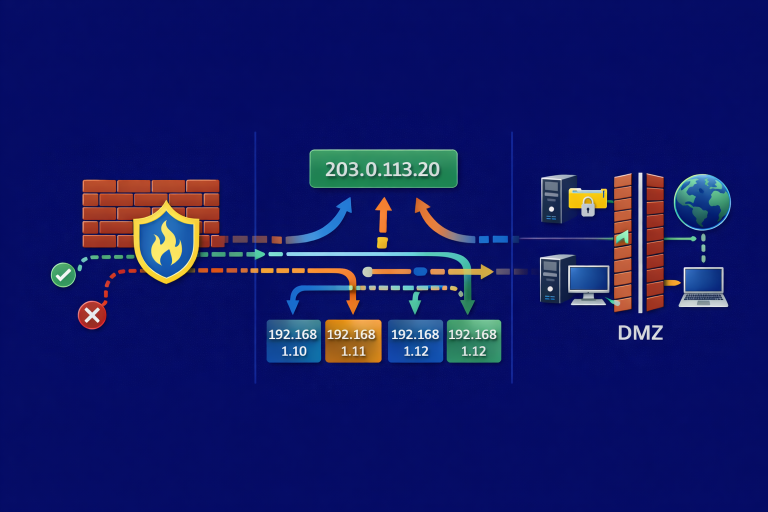
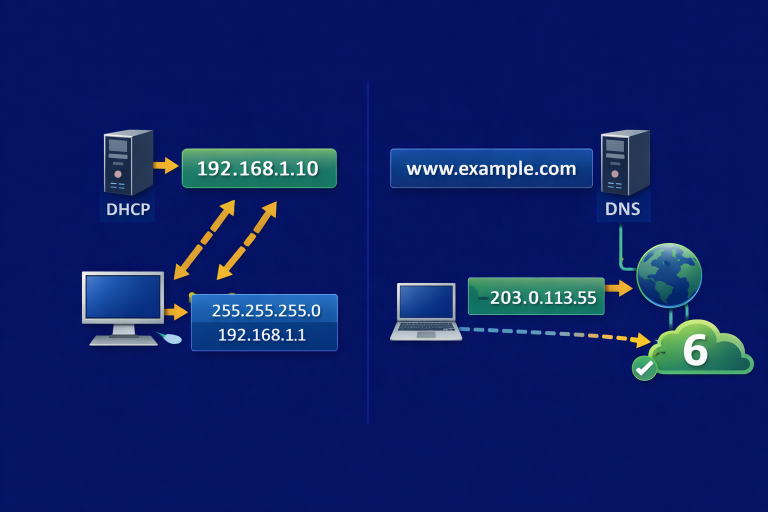
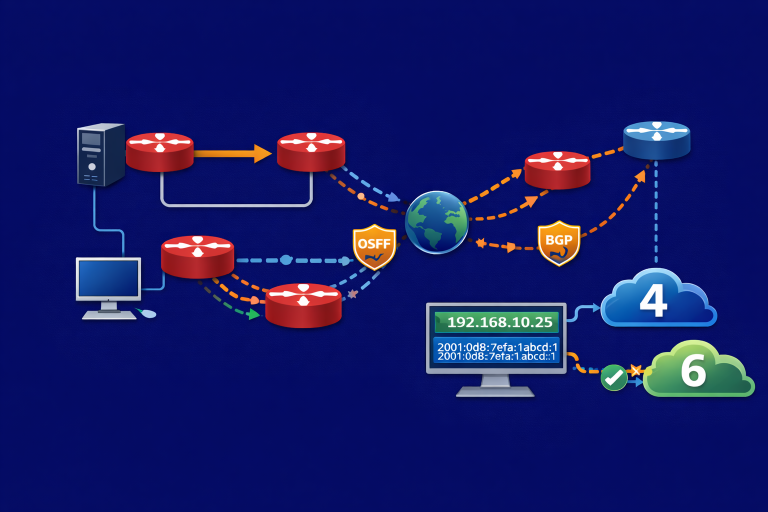
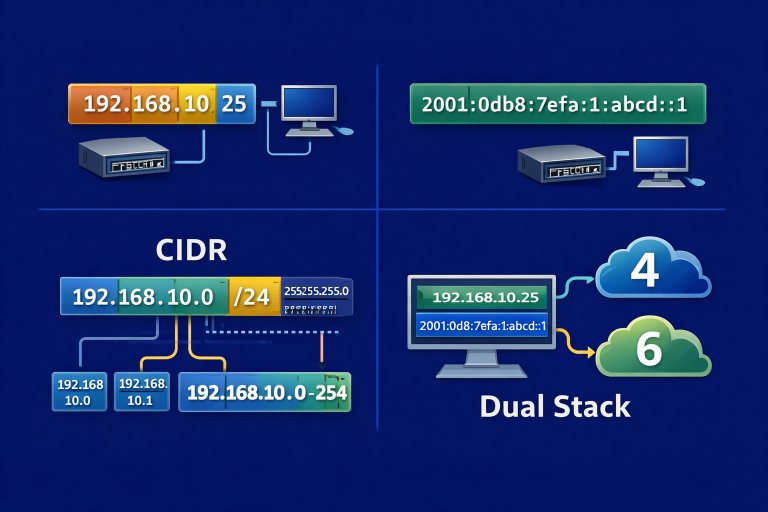
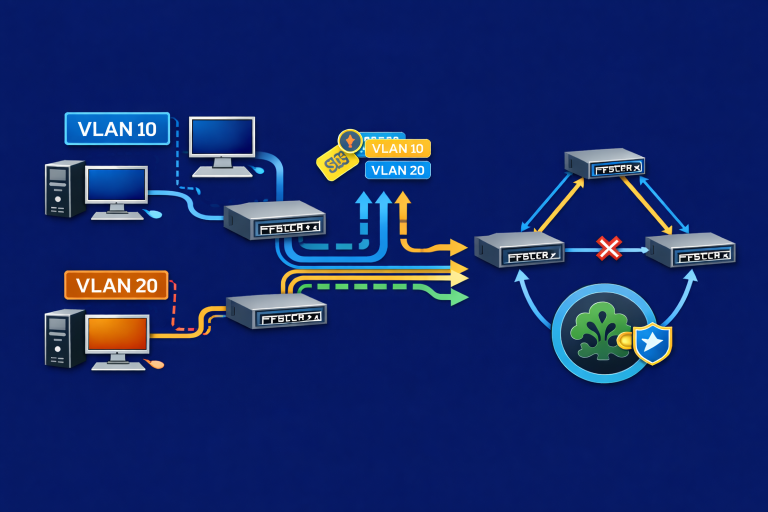
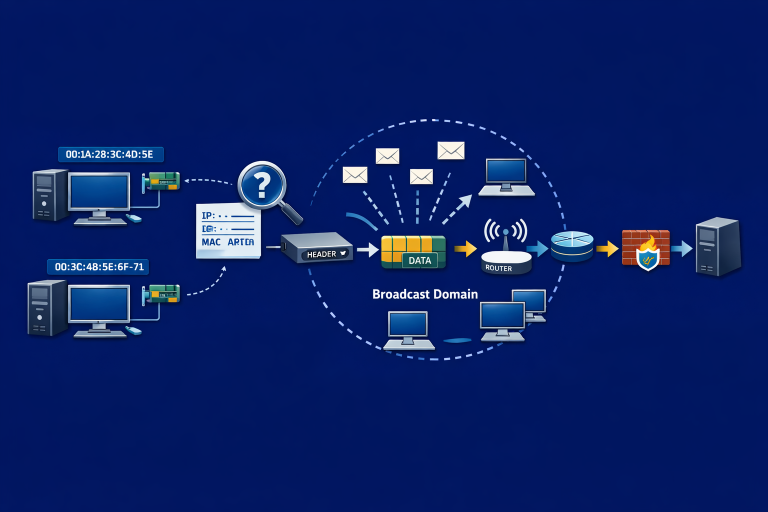
Sharing notes from my ongoing learning journey — what I build, break and understand along the way.

Why Kali Linux? Building a Safe Cybersecurity Lab in VirtualBox (Oracle VM)
Kali Linux on VirtualBox: Key Advantages, Features, and a Practical Workflow When the name Kali Linux comes up, a large part of the internet quickly steers the topic toward “hacking.” But what truly makes Kali valuable isn’t individual tools or…