Sharing notes from my ongoing learning journey — what I build, break and understand along the way.
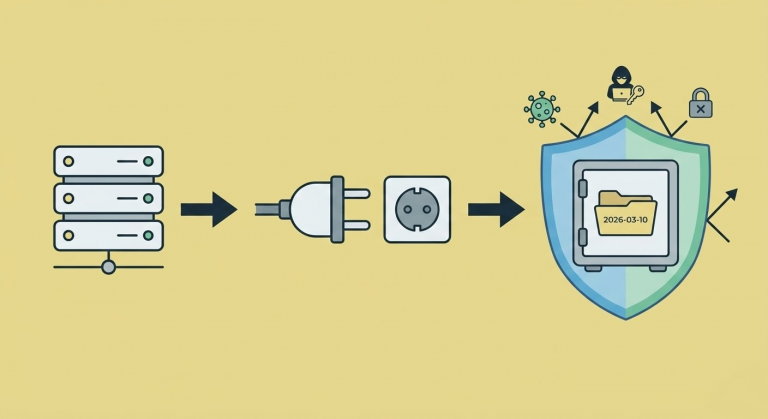
The Invisible Shield: Air-Gapped Backups vs Ransomware
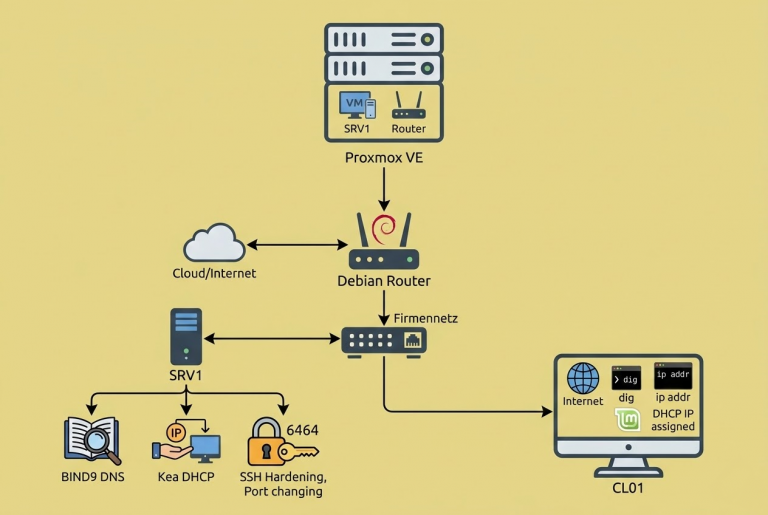
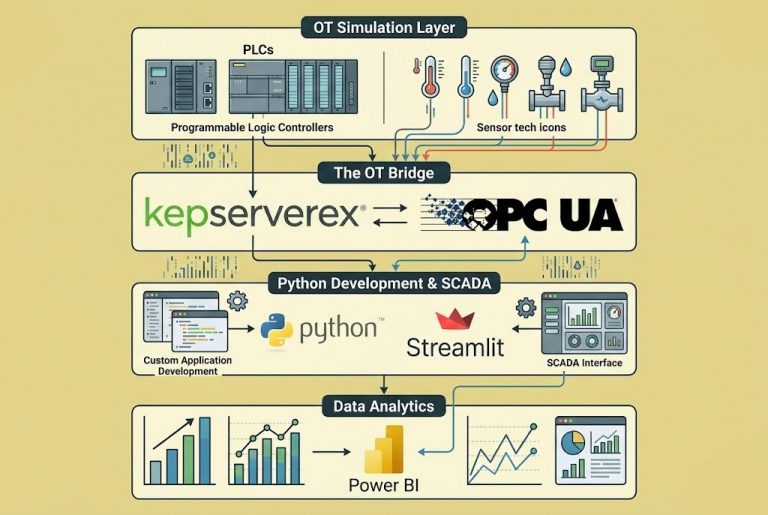
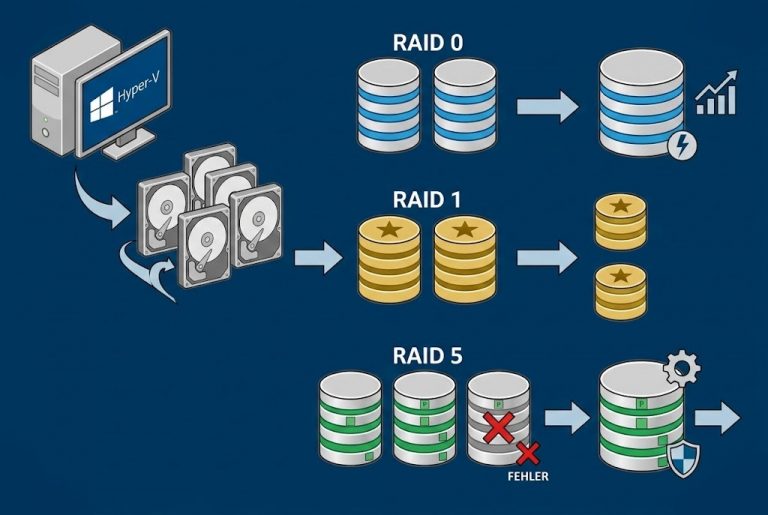
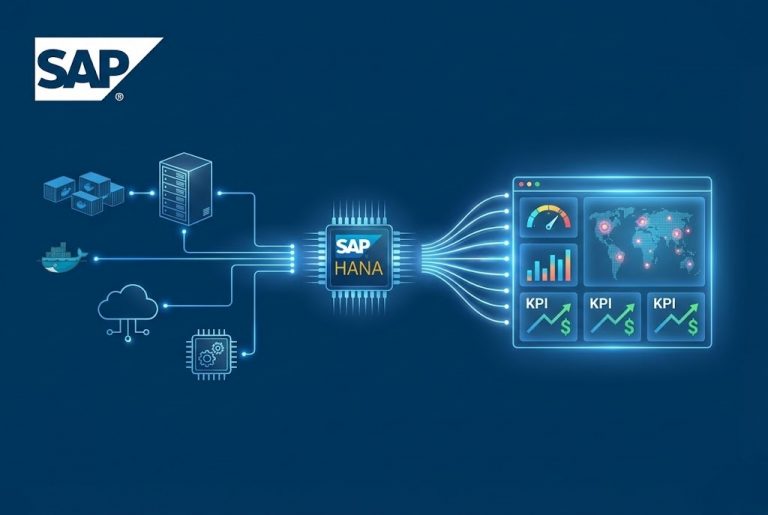
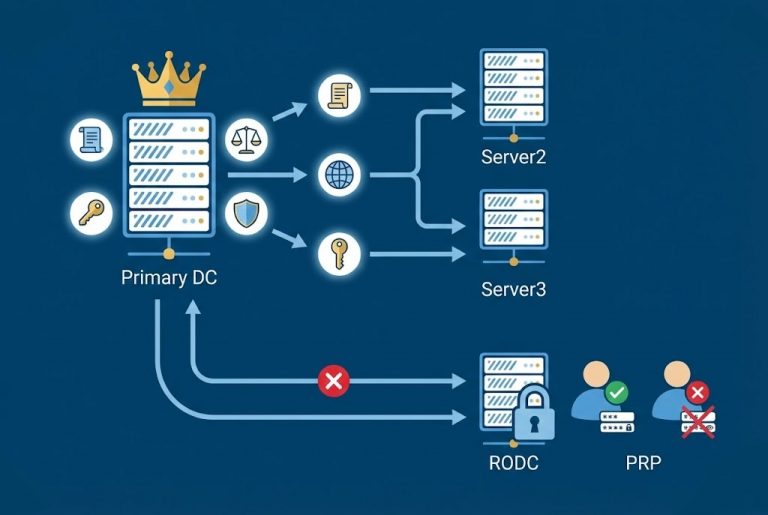
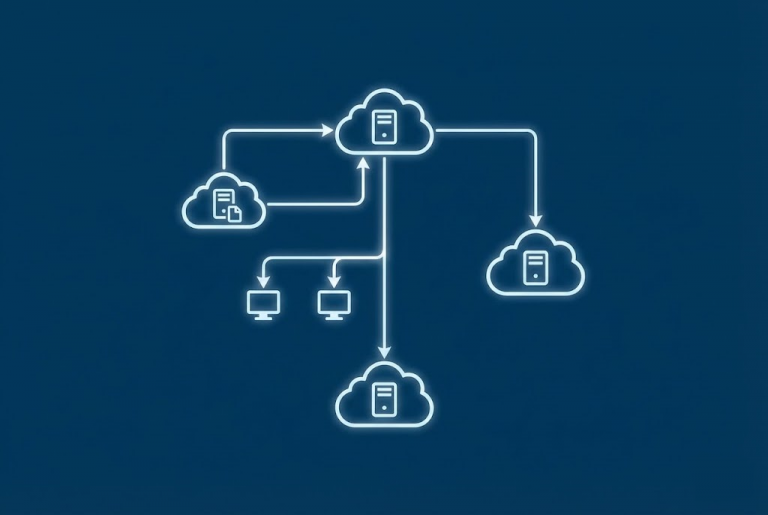
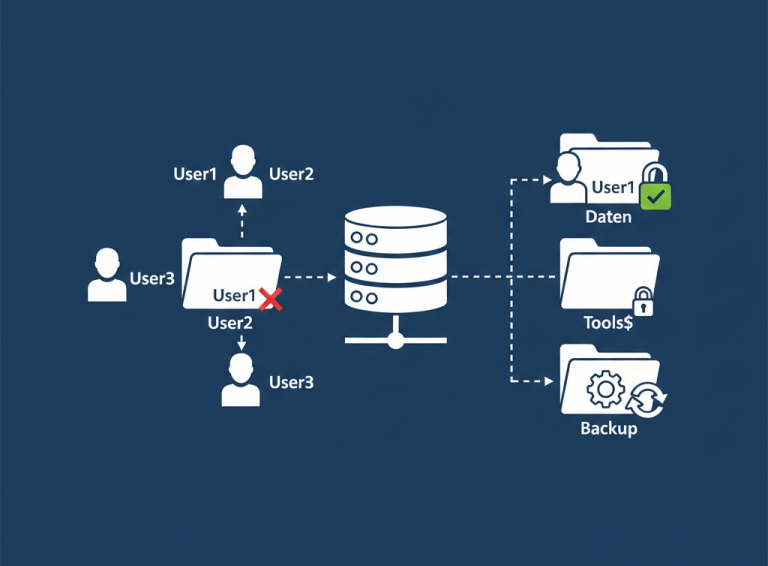
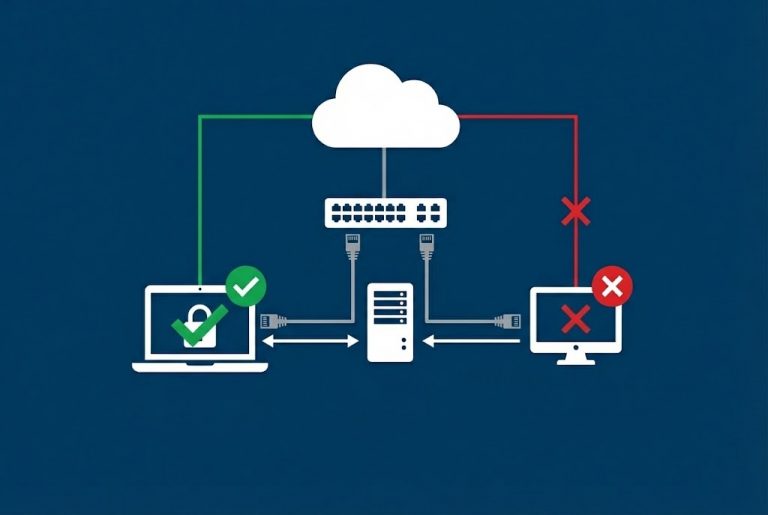
Building an Air-Gapped Automated Backup System with TrueNAS and iSCSI We live in a digital world, and whether we are a massive corporation or a small startup, our most valuable asset is our “data.” It has happened to all of…