Sharing notes from my ongoing learning journey — what I build, break and understand along the way.
How to Set Up an OpenVPN Server on Oracle Cloud Free Tier — Step-by-Step Guide for Beginners
Complete OpenVPN Deployment on Oracle Cloud Free Tier — From Network Setup to Secure Connection
As an IT student, I’m always looking for hands-on projects to improve my skills in system administration, network security, and cloud infrastructure. This project was my attempt to put theory into practice by setting up my own VPN server, allowing me to securely route and control my internet traffic.
Oracle Cloud’s Free Tier offering made it possible to experiment at no cost. My goal was to build everything from scratch — starting with a Virtual Cloud Network (VCN), preparing the infrastructure, then deploying an OpenVPN server and establishing a secure connection.
1. Pre-Instance Preparation — Network Configuration
Before creating a compute instance, the network side must be ready. In order for an instance to have a public IPv4 address, you need to set up a VCN, subnet, internet gateway, and route rules first.
1.1 Creating the VCN (Virtual Cloud Network)
- Go to Networking → Virtual Cloud Networks → Create VCN
- Name:
vpn-vcn(you can name it anything) - IPv4 CIDR Block:
10.0.0.0/16 - Leave IPv6 support disabled (not needed for this project).
1.2 Adding an Internet Gateway
- Gateways → Internet Gateway → Create Internet Gateway
- Name:
vpn-igw - Check Enable.
1.3 Route Table Setup
- Routing → Route tables → Default Route Table for vpn-vcn
- Add Route Rule:
- Destination CIDR Block:
0.0.0.0/0 - Target Type: Internet Gateway
- Target:
vpn-igw
- Destination CIDR Block:
1.4 Creating a Public Subnet
- Subnets → Create Subnet
- Name:
vpn-subnet - IPv4 CIDR Block:
10.0.0.0/24 - Subnet Type: Public Subnet
- Route Table: select the default route table we just updated
- Name:
- With a public subnet, the instance can be assigned a public IP.
2. Security Rules (Security Lists)
We need to open specific ports to access the instance.
VCN → Security Lists → Default Security List for vpn-vcn → Add Ingress Rules
- SSH (Management)
- Source CIDR:
0.0.0.0/0 - Protocol: TCP
- Destination Port Range: 22
- Source CIDR:
- OpenVPN (TCP/443)
- Source CIDR:
0.0.0.0/0 - Protocol: TCP
- Destination Port Range: 443
- Source CIDR:
- ICMP (Optional)
- Useful for ping and MTU adjustments.
- Source CIDR:
0.0.0.0/0 - Protocol: ICMP
3. Generating an SSH Key (On Your Local Machine)
To connect securely to the server, generate an SSH key pair.
Generate it locally on your own machine — never share your private key.
Linux / macOS / WSL:
ssh-keygen -t ed25519 -C "oracle-vpn-key"
- Private key:
~/.ssh/id_ed25519 - Public key:
~/.ssh/id_ed25519.pub
Windows PowerShell (if OpenSSH is installed):
ssh-keygen -t ed25519 -C "oracle-vpn-key"
Only upload the
.pubfile to Oracle — keep your private key safe.
4. Creating the Instance
Compute → Instances → Create Instance
- Name:
openvpn-server - Image: Ubuntu 22.04 LTS
- Shape: VM.Standard.E2.1.Micro (Always Free eligible)
- Placement: any availability domain
- Networking:
- VCN:
vpn-vcn - Subnet:
vpn-subnet - Public IPv4 Address: Automatically assign (must be checked)
- VCN:
- SSH Keys: choose Paste public key and paste the contents of your
.pubfile.
Once the instance is created, you’ll see its Public IPv4 in the details.
5. Connecting to the Server
From your local terminal:
ssh -i ~/.ssh/id_ed25519 ubuntu@SERVER_PUBLIC_IP
-ispecifies the path to your private key.ubuntuis the default user for Ubuntu images.
6. Installing OpenVPN
We’ll use the popular Nyr script to automate the installation.
sudo -s
apt-get update && apt-get -y install curl
curl -O https://raw.githubusercontent.com/Nyr/openvpn-install/master/openvpn-install.sh
chmod +x openvpn-install.sh
bash openvpn-install.sh
During setup:
- IP address: press Enter to accept the detected one.
- Protocol: TCP
- Port: 443
- DNS: Cloudflare (1.1.1.1) or Google (8.8.8.8)
- Client name: e.g.,
vpnclient
When finished, the .ovpn profile will be saved as /home/ubuntu/vpnclient.ovpn.
7. Downloading the .ovpn File to Your Local Machine
From your local terminal:
scp -i ~/.ssh/id_ed25519 ubuntu@SERVER_PUBLIC_IP:/home/ubuntu/vpnclient.ovpn .
The .ovpn file will now be available locally.
8. Connecting on Windows with OpenVPN Connect
- Download and install OpenVPN Connect.
- Click Import Profile → File and select your
.ovpnfile. - Click Connect.
9. Managing the VPN Service
On the server:
# Stop service
sudo systemctl stop openvpn-server@server
# Start service
sudo systemctl start openvpn-server@server
# Check status
sudo systemctl status openvpn-server@server
To add a new client, run:
sudo bash /root/openvpn-install.sh
Following these steps, I successfully deployed a fully functional OpenVPN server on Oracle Cloud Free Tier.
Starting from scratch with VCN, subnet, gateway, and security configurations helped me understand not just VPN setup but also the basics of network topology and cloud infrastructure.
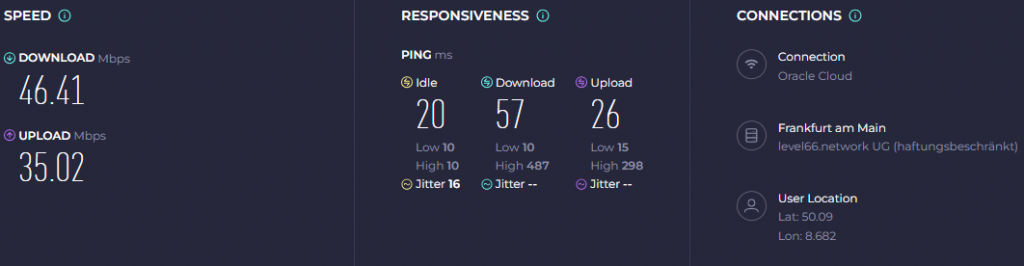
Speed Test Results
Speed test results will vary based on your ISP, VPN server location, and network conditions.