Sharing notes from my ongoing learning journey — what I build, break and understand along the way.
Secure IIoT Data Pipeline: WireGuard VPN & MQTT Hardening Guide
Implementation of a Secure Industrial Data Pipeline: VPN Tunneling and MQTT Broker Hardening
1. Introduction and Project Scope
In modern industrial environments, the secure transmission of telemetry data from field devices to central management systems is a critical requirement. This project focuses on the design and implementation of a secure End-to-End (E2E) data pipeline. The primary objective is to demonstrate how open-source tools can be integrated to meet industrial security standards, specifically focusing on network isolation and encrypted data transport.
As a student of Systems Integration , I have structured this project to address three primary technical challenges:
- Network-Level Security: Isolating IoT traffic from the general Local Area Network (LAN).
- Service Hardening: Configuring an MQTT broker to accept requests exclusively from authenticated users and via the secure tunnel.
- Data Simulation and Persistence: Generating structured industrial data and ensuring its availability for historical analysis.
2. Technical Architecture and Node Configuration
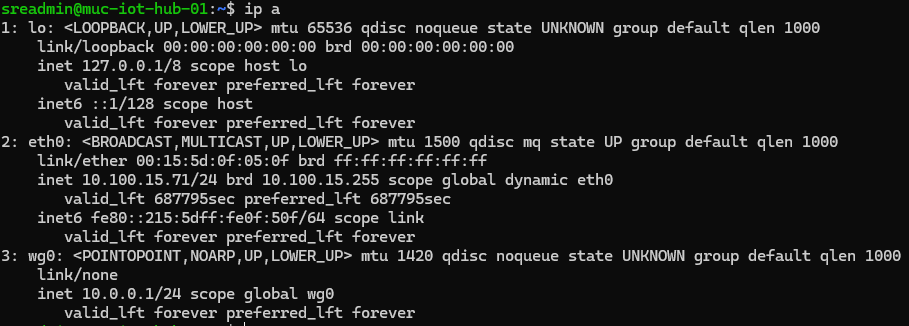
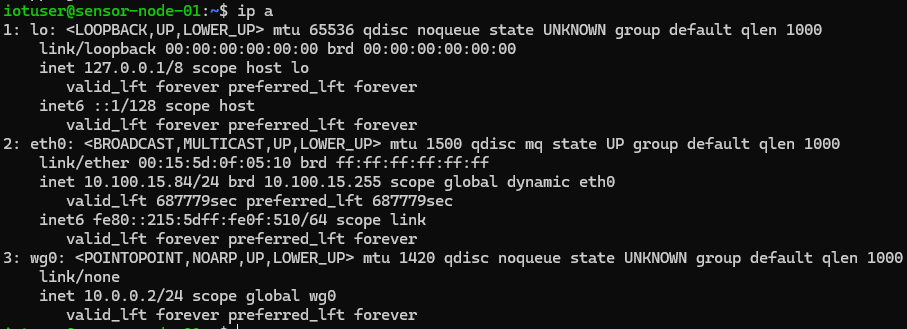
The infrastructure is built upon a dual-node architecture virtualized within a Hyper-V environment. Both nodes utilize Debian 11 (Bullseye) for its stability and minimal resource footprint in headless configurations.
- Central Hub (
muc-iot-hub-01): Serves as the primary data aggregator. It hosts the Mosquitto MQTT broker and manages the data persistence (historian) layer. - Sensor Node (
sensor-node-01): Acts as an Edge gateway, simulating a PLC (Programmable Logic Controller) or an industrial sensor interface via a Python script.
To achieve network-level isolation, a Virtual Private Network (VPN) based on the WireGuard protocol was implemented. This creates a virtual point-to-point interface, ensuring that telemetry traffic never traverses the physical LAN in plaintext.
3. Network Layer: WireGuard VPN Implementation
WireGuard was selected for this integration due to its kernel-level implementation and state-of-the-art cryptography (ChaCha20 and Poly1305). Unlike traditional SSL/TLS-based VPNs, WireGuard is connectionless and offers a significantly smaller attack surface.
3.1 Key Management: Security is established through asymmetric cryptography. Each node possesses a unique private key and a corresponding public key. Authentication is strictly limited to these pre-shared public keys (Peer-to-Peer).
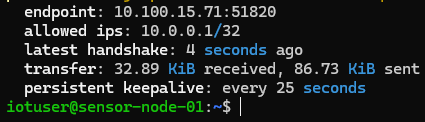
3.2 Configuration Details: The server node is configured to listen on a specific UDP port (51820). The configuration file (/etc/wireguard/wg0.conf) defines the allowed peer (the sensor node) and assigns internal static IPs (10.0.0.1 and 10.0.0.2).
A critical parameter in the client configuration is the PersistentKeepalive setting. In industrial network topologies involving firewalls or NAT (Network Address Translation), this ensures the tunnel remains active by sending a handshake packet every 25 seconds.
4. Middleware Layer: Hardening the MQTT Broker
The Eclipse Mosquitto broker serves as the message distribution engine. In its default state, an MQTT broker can be vulnerable to unauthorized subscriptions. To mitigate this, a multi-layer security approach was applied to the configuration located at /etc/mosquitto/mosquitto.conf.
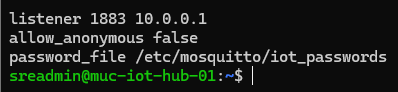
4.1 Interface Binding: To prevent external access from the physical network, the broker is explicitly bound to the VPN interface address (10.0.0.1). This ensures that the service is unreachable from any IP address not participating in the WireGuard tunnel.
4.2 Authentication and Access Control: Anonymous access has been disabled. A dedicated password file was generated using the mosquitto_passwd utility. This file stores credentials in a hashed format, requiring the edge node to provide a valid username and password for every session.
5. Application Layer: Industrial Data Simulation via Python
The data generation layer is implemented using a Python 3.x script utilizing the paho-mqtt library. The script is designed to simulate the behavior of an industrial machine through a controlled state-machine logic.
5.1 Data Structure (JSON): Data is transmitted in JSON (JavaScript Object Notation) format, the industry standard for interoperability. Each payload includes:
timestamp: For temporal synchronization.node_id: For device identification.data: A nested object containing Pressure (p), Temperature (t), and Vibration (v).status: A numerical system health indicator (0: Normal, 1: Warning, 2: Critical).
5.2 Sequential Error Logic: To test monitoring capabilities, the script follows a 120-second operational cycle, systematically triggering specific anomalies:
- Pressure Spikes: Simulating hydraulic overpressure.
- Thermal Fluctuations: Simulating cooling system inefficiencies.
- Vibration Anomalies: Simulating mechanical wear in rotating components.
6. Persistence Layer: Data Logging and Historian Functionality
For industrial compliance and post-incident forensics, data must be stored persistently. In this project, the tee utility is used on the server side to fork the incoming data stream. This allows for real-time monitoring while simultaneously appending every message to a centralized log file (industrial_production.log).
This file-based approach provides a foundation for future data analysis and ensures that even in the event of a service interruption, a chronological record of machine states is preserved.
7. Conclusion and Technical Assessment
The implementation of this secure IIoT pipeline successfully demonstrates the integration of multiple networking and security layers. By utilizing WireGuard for transport security and applying strict access controls to the MQTT broker, the system achieves a high level of resilience against common network-based threats.
From a Systems Integration perspective, this project validates several core principles:
- Network-layer encryption is significantly more robust than relying solely on application-level security.
- Static IP assignment and interface binding effectively reduce the internal attack surface.
- Structured logging is an essential requirement for predictive maintenance and industrial auditing.
