Sharing notes from my ongoing learning journey — what I build, break and understand along the way.
VPN and Tunneling Explained: How They Work, Protocols, and Anonymity
Understanding VPN and Tunneling in Depth
What Is a VPN?
A VPN (Virtual Private Network) is a method of creating a secure, encrypted, and logical “private network” over an untrusted network (most commonly the internet).
Its main goals are:
- Confidentiality: Your data is encrypted so third parties cannot see it.
- Integrity: If the data is altered in transit, it can be detected.
- Authentication: You can be sure that the party you are communicating with is genuine.
Common Uses of VPNs
- Remote Access VPN: A person working from home connects securely to the corporate network.
- Site-to-Site VPN: Two branch or office networks are securely joined over the internet.
- Privacy VPNs: Everyday users hide their IP address or bypass geo-restrictions using commercial VPN services.
What Is Tunneling?
Tunneling is the process of encapsulating one network protocol inside another. Simply put:
- You take the original packet you want to send.
- You place it inside another protocol’s packet.
- On the receiving end, the wrapper is removed and the original data is extracted.
Why Tunneling Matters
- Protocol Transport: You can carry protocols that are not normally supported (e.g., IPv6 traffic inside an IPv4 backbone).
- Security: You can hide data inside an encrypted capsule to prevent eavesdropping.
- Network Virtualization: You can connect two remote networks as if they were on the same local LAN.
Tunneling is the foundation of VPN. A VPN establishes a secure tunnel and sends your traffic through it.
The Relationship Between VPN and Tunneling
You can think of VPN as:
- VPN = Tunneling + Encryption + Authentication
So a VPN doesn’t just create a tunnel; it ensures that the tunnel is secure, encrypted, and authenticated.
Example:
Traffic from a branch office to headquarters would normally travel across the internet in the open. With VPN:
- The LAN packet is encapsulated inside the VPN tunnel.
- It is encrypted.
- At the other end, it is decrypted, unwrapped, and delivered to the destination.
Tunneling Protocols Used in VPNs
1. IPsec (Internet Protocol Security)
- One of the most widely used secure tunneling methods.
- Encrypts and authenticates IP packets.
- Uses IKE (Internet Key Exchange) for key exchange.
- Modes: Transport Mode (only payload encrypted) and Tunnel Mode (entire packet encapsulated).
- Standard choice for site-to-site VPNs.
2. SSL/TLS VPN
- Built on HTTPS.
- Allows users to connect through a browser or lightweight client.
- Often used for remote access VPNs.
- Advantage: Port 443 is almost always open, making it easy to work anywhere.
3. PPTP (Point-to-Point Tunneling Protocol)
- An old Microsoft protocol.
- Considered insecure today and not recommended.
4. L2TP (Layer 2 Tunneling Protocol) + IPsec
- L2TP creates the tunnel, IPsec encrypts it.
- Still in use but gradually being replaced by newer options.
5. OpenVPN
- Open-source, SSL/TLS-based VPN protocol.
- Works over both TCP and UDP.
- Highly popular for its flexibility and strong security.
6. WireGuard
- A modern VPN protocol.
- Lightweight, fast, and based on modern cryptography.
- Integrated into the Linux kernel and widely adopted on mobile platforms.
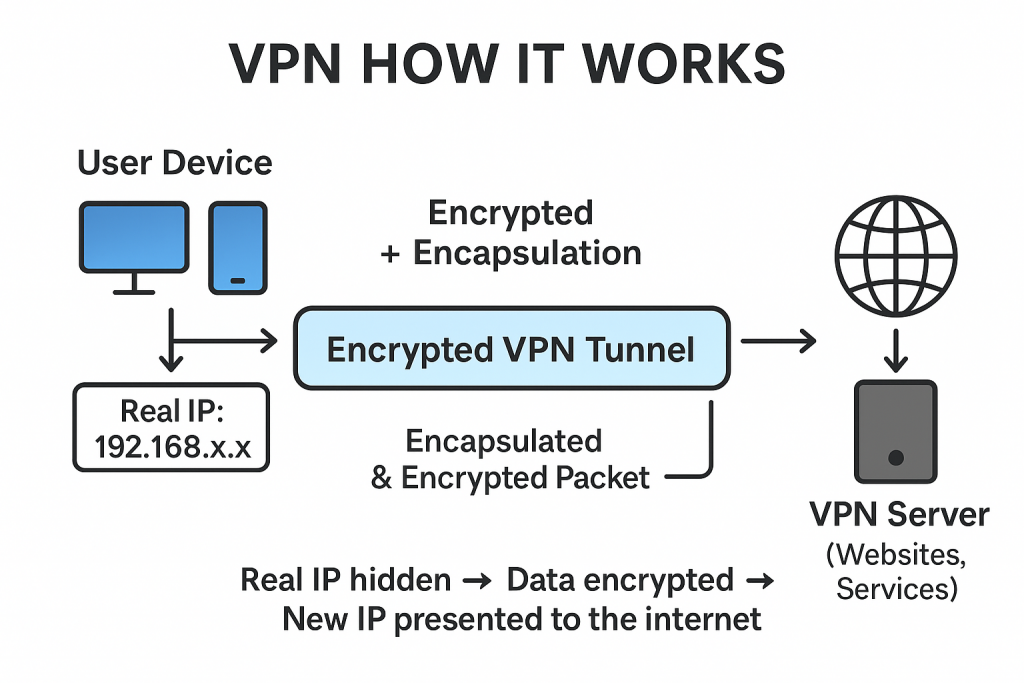
How Does a VPN Work? (Step by Step)
When a user clicks “Connect” on their VPN client, here is what happens behind the scenes:
- Connection Initiation:
The client contacts the VPN server to request a connection. - Authentication:
- The user verifies their identity (username/password, certificate, or token).
- The server also proves its identity (certificate, CA).
- Key Exchange and Encryption Setup:
- The client and server securely establish session keys.
- These keys will encrypt and decrypt the traffic.
- Tunnel Establishment:
- Original traffic (e.g., an HTTP request) is taken.
- It is placed into a VPN tunnel (IPsec, OpenVPN, WireGuard, etc.).
- It is encrypted and sent across the internet.
- Decryption on the Other Side:
- The VPN server receives the packet, decrypts it, removes the wrapper.
- The original data is then forwarded to its destination (e.g., a website, a corporate server).
- Response Back:
- The destination responds.
- The VPN server encrypts and encapsulates the reply.
- It travels back through the tunnel, is decrypted by the client, and reaches the user’s application.
- IP Masking:
To the outside world, the traffic appears to originate from the VPN server’s IP address, not the user’s real IP.
All of this happens in milliseconds. To the user, the only visible thing is “VPN connected,” but under the hood, a complex security process is taking place.
VPN and Anonymity
One of the most common reasons people use VPNs in everyday life is to “stay anonymous.” When you connect to a VPN, you get a new IP address and appear to be online from a different location. But is this really enough for anonymity?
What a VPN Does Provide
- IP Masking: Websites see the VPN server’s IP, not your real one.
- Encrypted Traffic: Your ISP and random third parties cannot easily inspect your traffic.
- Bypass Geo-Restrictions: You can appear to be connecting from another country.
The Limitations of VPN
- Not True Anonymity: The VPN provider itself knows your real IP. If logs are kept, your identity can be linked.
- Browser Tracking Still Exists: Cookies, fingerprinting, or browsing while logged into accounts like Google continue regardless of VPN.
- Legal Pressure: Some VPN companies may comply with authorities and share information.
For Real Anonymity
A VPN alone is not enough. Stronger anonymity requires:
- Tor network (with or without VPN),
- Ad/tracker blockers,
- Anonymous emails and identity practices.
In short, VPN hides you from your ISP and casual observers, and it masks your IP, but it does not make you completely anonymous.
In Short
- Tunneling is the technique of wrapping one protocol inside another.
- VPN adds encryption and authentication to tunneling, making it secure.
- Protocols like IPsec, SSL/TLS, OpenVPN, and WireGuard form the backbone of VPN technology.
- When you connect to a VPN, the process includes authentication, key exchange, tunnel creation, and encryption.
- A VPN changes your IP and increases your privacy, but it does not guarantee complete anonymity.
