Sharing notes from my ongoing learning journey — what I build, break and understand along the way.
What is TLS/SSL? The Basics of Secure Communication on the Web
TLS vs SSL: How It Works and Why It Matters
When sending and receiving data on the internet, there are three basic things we want:
- Confidentiality: Only the sender and receiver can see the data.
- Integrity: The data must not be altered while in transit.
- Authentication: The other side really is the server it claims to be.
SSL (Secure Sockets Layer) was originally created to meet these needs. However, SSL is now outdated and insecure. It has been replaced by TLS (Transport Layer Security). Even though people still say “SSL certificate,” the protocol in use today is TLS.
Core Concepts
- Symmetric encryption: The same key is used for both encrypting and decrypting (e.g., AES, ChaCha20). It’s fast, and the actual data is transmitted this way.
- Asymmetric encryption: Public key + private key system (e.g., RSA, ECDSA). Used for key exchange and digital signatures.
- Certificates and CAs: A Certificate Authority (CA) validates the server’s identity and signs it. Browsers trust these authorities.
TLS Handshake
TLS 1.3 (the most recent version)
- The client says hello: “I support these versions and ciphers.”
- The server replies: “Okay, let’s use this version and cipher, here’s my certificate.”
- They perform an ephemeral key exchange (ECDHE) and derive a shared secret.
- From this point, all traffic is encrypted with a symmetric key.
TLS 1.3 simplified the process, making it faster and more secure.
TLS 1.2 (still common)
The logic is similar but with more steps. For security, the recommended setup is ECDHE + AES-GCM. RSA key exchange is no longer advised.
Types of Certificates
- DV (Domain Validated): Confirms control of the domain. Sufficient for most websites.
- OV / EV: Also verify organizational details. Security is the same, but they provide more corporate identity visibility.
- SAN (Subject Alternative Name): Lists the domains the certificate is valid for. CN alone is no longer enough.
- Wildcard: Covers subdomains (e.g.,
*.example.com), but not the root domain itself.
For the key type, either RSA (at least 2048 bits) or ECDSA (P-256) is used. ECDSA is faster and lighter, but not all clients support it.
Cipher Suites
A TLS connection uses a combination of:
- Key exchange: ECDHE (provides forward secrecy).
- Certificate algorithm: RSA or ECDSA.
- Symmetric cipher: AES-GCM or ChaCha20-Poly1305.
- Hash function: SHA-2 family.
For a secure connection, the must-have is: ECDHE + AEAD (AES-GCM or ChaCha20-Poly1305).
TLS 1.3’s 0-RTT Feature
TLS 1.3 introduced the “0-RTT” feature, allowing a client reconnecting to a server it already knows to send data in the very first message. This improves performance. However, this data can be replayed (replay attack), so it should not be used for sensitive or critical actions.
Common Security Mistakes
- Leaving older versions (SSLv3, TLS 1.0, TLS 1.1) enabled makes the server vulnerable.
- Forgetting to include intermediate certificates causes browser errors.
- Allowing RSA key exchange prevents forward secrecy.
- Enabling TLS compression opens the door to CRIME/BREACH attacks.
- Enabling HSTS preload without testing can lock you out of your own domain.
Testing and Verification
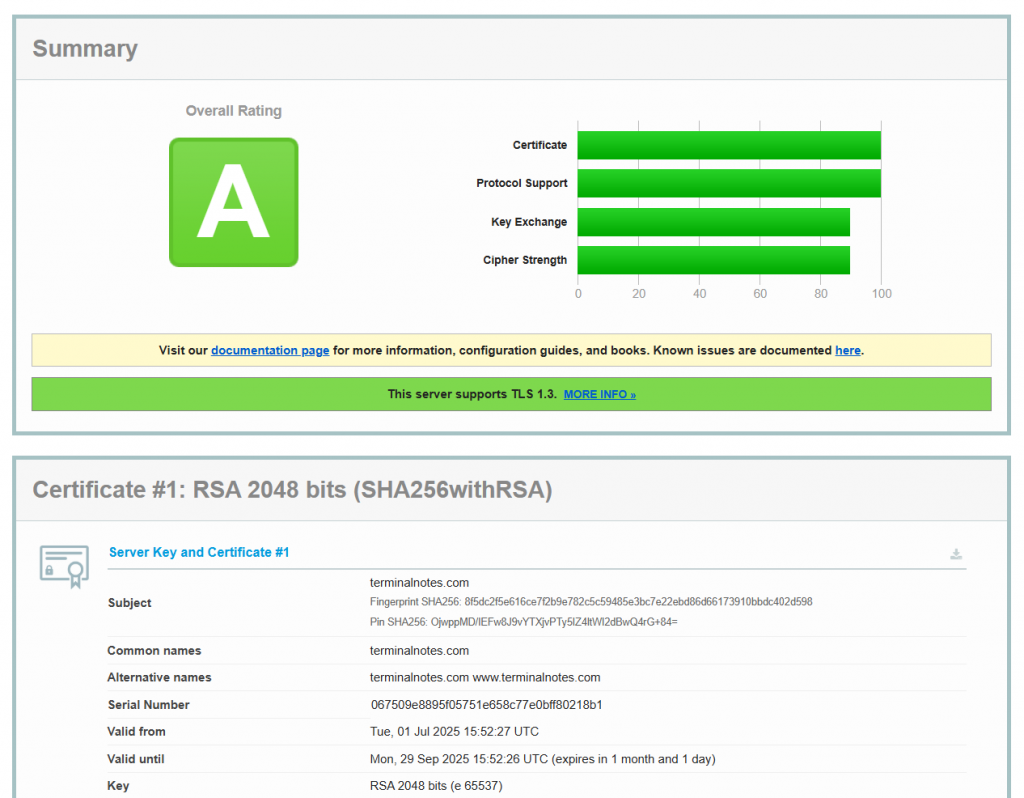
- SSL Labs Test: Use Qualys SSL Labs to test your site. Aim for an A+ rating.
I tested my own site and received an A. The certificate is correctly installed, TLS 1.3 is enabled, and secure ciphers are active. To reach A+, I need to enable HSTS and OCSP stapling.
- testssl.sh: Run this in the command line for a detailed scan.
- Browser tools: Check the TLS version, certificate details, and HTTP/2/HTTP/3 support directly in developer tools.
In Short
TLS/SSL is the backbone of secure communication on the internet. With the right configuration, it protects users’ data and increases trust in your website. For a secure setup today, you should:
- Allow only TLS 1.2 and 1.3,
- Use ECDHE + AES-GCM or ChaCha20-Poly1305 ciphers,
- Have a certificate with the correct SAN entries,
- Include intermediate certificates in the chain,
- Enable HSTS and OCSP stapling,
- Keep testing regularly to stay up to date.
