Sharing notes from my ongoing learning journey — what I build, break and understand along the way.
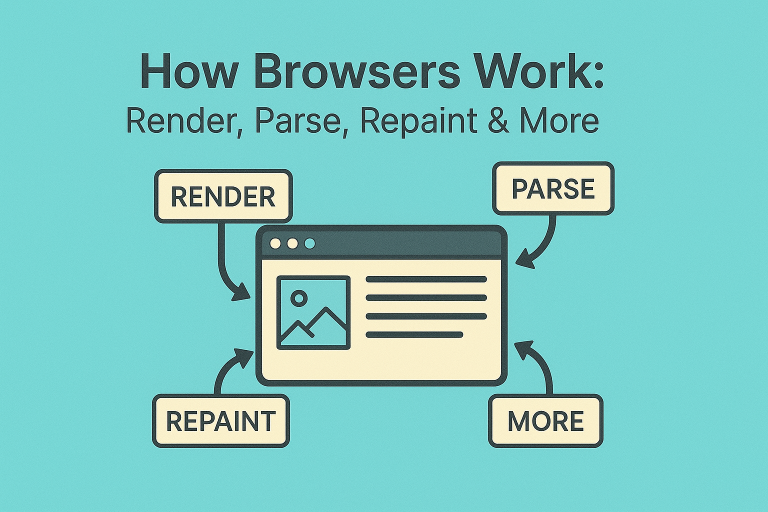
How Browsers Work: Understanding Rendering, Parsing, and Repainting
How Browsers Work: Render, Parse, and Repaint Explained Every webpage we see is the result of a complex process happening behind the scenes inside our browser. Clicking a link and seeing a page appear looks simple — but under the…